[ad_1]

Getty Pictures
Professional-Russian risk actors are persevering with their unrelenting pursuit of Ukrainian targets, with an array of campaigns that embody pretend Android apps, hack assaults exploiting essential vulnerabilities, and e mail phishing assaults that try to reap login credentials, researchers from Google stated.
One of many newer campaigns got here from Turla, a Russian-speaking superior persistent risk actor that has been energetic since no less than 1997 and is among the many most technically refined on this planet. According to Google, the group focused pro-Ukrainian volunteers with Android apps that posed as launchpads for performing denial-of-service assaults in opposition to Russian web sites.
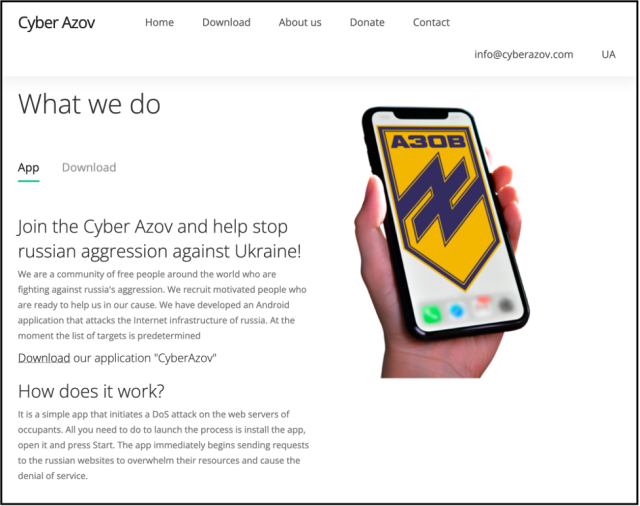
“All you must do to launch the method is set up the app, open it and press begin,” the pretend web site selling the app claimed. “The app instantly begins sending requests to the Russian web sites to overwhelm their sources and trigger the denial of service.”
In reality, a researcher with Google’s risk evaluation group stated, the app sends a single GET request to a goal web site. Behind the scenes, a special Google researcher told Vice that the app was designed to map out the consumer’s Web infrastructure and “work out the place the folks which can be doubtlessly doing these types of assaults are.”
The apps, hosted on a website spoofing the Ukrainian Azov Regiment, mimicked one other Android app Google first noticed in March that additionally claimed to carry out DoS assaults in opposition to Russian websites. Not like the Turla apps, stopwar.apk, because the latter app was named, despatched a steady stream of requests till the consumer stopped them.
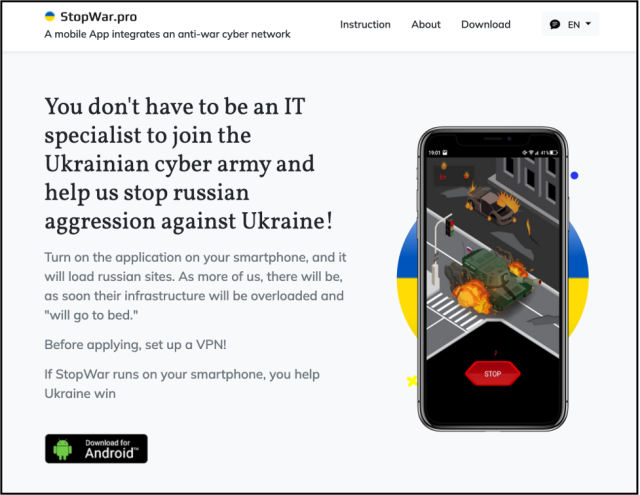
“Primarily based on our evaluation, we imagine that the StopWar app was developed by pro-Ukrainian builders and was the inspiration for what Turla actors based mostly their pretend CyberAzov DoS app off of,” Google researcher Billy Leonard wrote.
Different hacking teams sponsored by the Kremlin have additionally focused Ukrainian teams. Campaigns included the exploitation of Follina, the title given to a essential vulnerability in all supported variations of Home windows that was actively targeted in the wild for greater than two months as a zero-day.
Google researchers confirmed a CERT-UA report from June that stated a special Kremlin-sponsored hacking group—tracked below quite a lot of names together with Fancy Bear, often known as Pawn Storm, Sofacy Group, and APT28—was additionally exploiting Follina in an try and infect targets with malware often known as CredoMap. Moreover, Google stated that Sandworm—one more group sponsored by the Russian authorities—was additionally exploiting Follina. That marketing campaign used compromised authorities accounts to ship hyperlinks to Microsoft Workplace paperwork hosted on compromised domains, primarily focusing on media organizations in Ukraine.
CERT-UA
Safety agency Palo Alto Networks, in the meantime, reported on Tuesday that Russia’s Cloaked Ursa hacking group (also called APT29, Nobelium, and Cozy Bear) had additionally stepped up malware assaults for the reason that begin of Russia’s invasion of Ukraine, partially by making malicious recordsdata for obtain obtainable on Dropbox and Google Drive. US and UK intelligence companies have publicly attributed APT29 to Russia’s International Intelligence Service (SVR).
“This aligns with the group’s historic focusing on focus, relationship again to malware campaigns in opposition to Chechnya and different former Soviet bloc international locations in 2008,” Palo Alto Networks researchers Mike Harbison and Peter Renals wrote. Extra lately, APT29 has been linked to a hack of the US Democratic National Committee found in 2016 and the SolarWinds supply-chain attacks from 2020.
Not all of the risk teams focusing on Ukraine are Kremlin-sponsored, Google stated. Just lately, a financially motivated actor tracked as UAC-0098 impersonated the State Tax Service of Ukraine and delivered malicious paperwork that tried to use Follina. Google stated the actor is a former preliminary ransomware entry dealer that beforehand labored with the Conti ransomware group.
On Wednesday, the US Cyber Command shared technical particulars associated to what the company stated are a number of sorts of malware focusing on Ukrainian entities in current months. The malware samples can be found on VirusTotal, Pastebin, and GitHub. Safety agency Mandiant said two separate espionage teams used the malware, one tracked as UNC1151 and attributed by Mandiant to the Belarusian authorities and the opposite tracked as UNC2589, which the agency stated is “believed to behave in help of Russian authorities curiosity and has been conducting intensive espionage assortment in Ukraine.”
The European Union also called out the Russian government this week, noting {that a} current distributed denial-of-service marketing campaign was solely the most recent instance of cyberattacks it launched since its invasion.
“Russia’s unprovoked and unjustified navy aggression in opposition to Ukraine has been accompanied by a big enhance of malicious cyber actions, together with by a placing and regarding variety of hackers and hacker teams indiscriminately focusing on important entities globally,” EU officers wrote. “This enhance in malicious cyber actions, within the context of the conflict in opposition to Ukraine, creates unacceptable dangers of spillover results, misinterpretation, and doable escalation.”
Source link


