[ad_1]

It’s not the type of safety discovery that occurs usually. A beforehand unknown hacker group used a novel backdoor, top-notch commerce craft, and software program engineering to create an espionage botnet that was largely invisible in lots of sufferer networks.
The group, which safety agency Mandiant is looking UNC3524, has spent the previous 18 months burrowing into victims’ networks with uncommon stealth. In instances the place the group is ejected, it wastes no time reinfecting the sufferer surroundings and selecting up the place issues left off. There are various keys to its stealth, together with:
- the usage of a novel backdoor Mandiant calls Quietexit, which runs on load balancers, wi-fi entry level controllers, and different kinds of IoT units that don’t assist antivirus or endpoint detection. This makes detection via conventional means troublesome
- personalized variations of the backdoor that use file names and creation dates which are much like respectable information used on a particular contaminated machine
- a live-off-the-land method that favors widespread Home windows programming interfaces and instruments over customized code with the purpose of leaving as mild a footprint as potential
- an uncommon means a second-stage backdoor connects to attacker-controlled infrastructure by, in essence, appearing as a TLS-encrypted server that proxies information via the SOCKS protocol
A tunneling fetish with SOCKS
In a post, Mandiant researchers Doug Bienstock, Melissa Derr, Josh Madeley, Tyler McLellan, and Chris Gardner wrote:
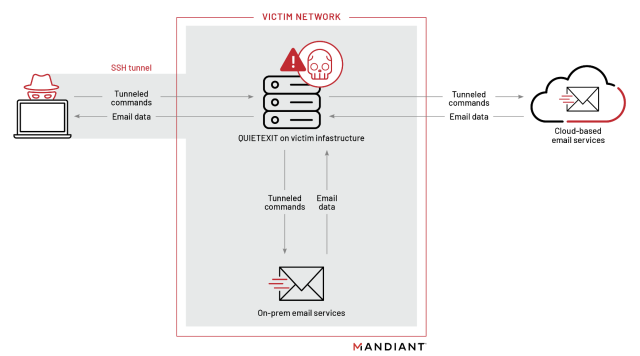
All through their operations, the risk actor demonstrated refined operational safety that we see solely a small variety of risk actors reveal. The risk actor evaded detection by working from units within the sufferer surroundings’s blind spots, together with servers working unusual variations of Linux and community home equipment working opaque OSes. These units and home equipment had been working variations of working programs that had been unsupported by agent-based safety instruments, and infrequently had an anticipated stage of community visitors that allowed the attackers to mix in. The risk actor’s use of the QUIETEXIT tunneler allowed them to largely dwell off the land, with out the necessity to herald extra instruments, additional lowering the chance for detection. This allowed UNC3524 to stay undetected in sufferer environments for, in some instances, upwards of 18 months.
The SOCKS tunnel allowed the hackers to successfully join their management servers right into a sufferer’s community the place they may then execute instruments with out leaving traces on any of the sufferer computer systems.
Mandiant
A secondary backdoor offered an alternate technique of entry to contaminated networks. It was primarily based on a model of the respectable reGeorg webshell that had been closely obfuscated to make detection more durable. The risk actor used it within the occasion the first backdoor stopped working. The researchers defined:
As soon as contained in the sufferer surroundings, the risk actor hung out to establish internet servers within the sufferer surroundings and guarantee they discovered one which was Web accessible earlier than copying REGEORG to it. Additionally they took care to call the file in order that it blended in with the applying working on the compromised server. Mandiant additionally noticed situations the place UNC3452 used timestomping [referring to a software out there here for deleting or modifying timestamp-related info on information] to change the Normal Info timestamps of the REGEORG internet shell to match different information in the identical listing.
One of many methods the hackers keep a low profile is by favoring normal Home windows protocols over malware to maneuver laterally. To maneuver to programs of curiosity, UNC3524 used a personalized model of WMIEXEC, a software that makes use of Home windows Administration Instrumentation to ascertain a shell on the distant system.
Finally, Quietexit executes its remaining goal: accessing e mail accounts of executives and IT personnel in hopes of acquiring paperwork associated to issues like company growth, mergers and acquisitions, and enormous monetary transactions.
“As soon as UNC3524 efficiently obtained privileged credentials to the sufferer’s mail surroundings, they started making Alternate Internet Companies (EWS) API requests to both the on-premises Microsoft Alternate or Microsoft 365 Alternate On-line surroundings,” the Mandiant researchers wrote. “In every of the UNC3524 sufferer environments, the risk actor would goal a subset of mailboxes….”
Source link


