[ad_1]

Final August, tutorial researchers found a potent new methodology for knocking websites offline: a fleet of misconfigured servers greater than 100,000 sturdy that may amplify floods of junk knowledge to once-unthinkable sizes. These assaults, in lots of instances, might end in an infinite routing loop that causes a self-perpetuating flood of site visitors. Now, content-delivery community Akamai says attackers are exploiting the servers to focus on websites within the banking, journey, gaming, media, and web-hosting industries.
These servers—generally known as middleboxes—are deployed by nation-states corresponding to China to censor restricted content material and by massive organizations to dam websites pushing porn, playing, and pirated downloads. The servers fail to comply with transmission control protocol specs that require a three-way handshake—comprising an SYN packet despatched by the shopper, a SYN+ACK response from the server, adopted by a affirmation ACK packet from the shopper—earlier than a connection is established.
This handshake limits the TCP-based app from being abused as amplifiers as a result of the ACK affirmation should come from the gaming firm or different goal quite than an attacker spoofing the goal’s IP tackle. However given the necessity to deal with uneven routing, by which the middlebox can monitor packets delivered from the shopper however not the ultimate vacation spot that’s being censored or blocked, many such servers drop the requirement by design.
A hidden arsenal
Final August, researchers on the College of Maryland and the College of Colorado at Boulder published research exhibiting that there have been a whole lot of 1000’s of middleboxes that had the potential to ship among the most crippling distributed denial of service assaults ever seen.
For many years, folks have used DDoSes to flood websites with extra site visitors or computational requests than the websites can deal with, denying providers to reliable customers. DDoSes are much like the previous prank of directing extra calls to the pizza parlor than the parlor has cellphone strains to deal with.
To maximise the injury and preserve assets, DDoSers usually enhance the firepower of their assaults although amplification vectors. Amplification works by spoofing the goal’s IP tackle and bouncing a comparatively small quantity of information at a misconfigured server used for resolving domains, syncing pc clocks, or rushing up database caching. As a result of the response the servers mechanically ship are dozens, a whole lot, or 1000’s of instances greater than the request, the response overwhelms the spoofed goal.
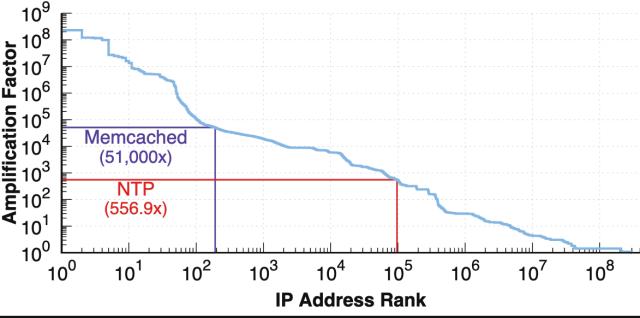
The researchers mentioned that a minimum of 100,000 of the middleboxes they recognized exceeded the amplification elements from DNS servers (about 54x) and Community Time Protocol servers (about 556x). The researchers mentioned that they recognized a whole lot of servers that amplified site visitors at a better multiplier than misconfigured servers utilizing memcached, a database caching system for rushing up web sites that may enhance site visitors quantity by an astounding 51,000x.
Listed here are two illustrations that present how the assaults work:
Bock et al.
Day of reckoning
The researchers mentioned on the time that that they had no proof of middlebox DDoS amplification assaults getting used actively within the wild however anticipated it will solely be a matter of time till that occurred.
On Tuesday, Akamai researchers reported that day has come. Over the previous week, the Akamai researchers mentioned, they’ve detected a number of DDoSes that used middleboxes exactly the way in which the tutorial researchers predicted. The assaults peaked at 11Gbps and 1.5 million packets per second.
Whereas small when in comparison with the biggest DDoSes, each groups of researchers count on the assaults to get bigger as DDoSers start to optimize their assaults and determine extra middleboxes that may be abused (the tutorial researchers didn’t launch that knowledge to forestall it from being abused).
Kevin Bock, the lead researcher behind final August’s research paper, mentioned DDoSers had loads of incentives to breed the assaults his crew theorized.
“Sadly, we weren’t stunned,” he informed me upon studying of the lively assaults. “We anticipated that it was solely a matter of time till these assaults have been being carried out within the wild as a result of they’re straightforward and extremely efficient. Maybe worst of all, the assaults are new; consequently, many operators don’t but have defenses in place, which makes it that rather more attractive to attackers.”
One of many middleboxes acquired a SYN packet with a 33-byte payload and responded with a 2,156-byte reply.
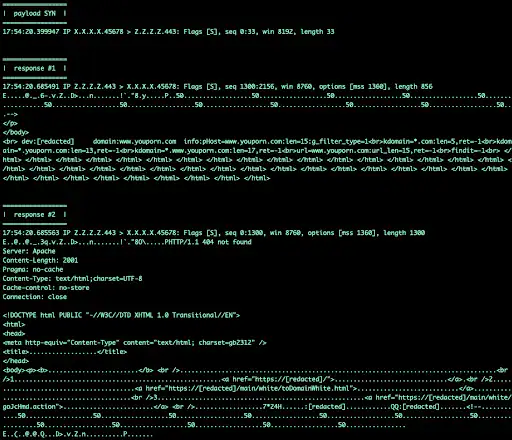
Akamai
That translated to an element of 65x, however the amplification has the potential to be a lot better with extra work.
Akamai researchers wrote:
Volumetric TCP assaults beforehand required an attacker to have entry to quite a lot of machines and quite a lot of bandwidth, usually an enviornment reserved for very beefy machines with high-bandwidth connections and supply spoofing capabilities or botnets. It is because till now there wasn’t a big amplification assault for the TCP protocol; a small quantity of amplification was doable, nevertheless it was thought-about nearly negligible, or on the very least subpar and ineffectual in comparison with the UDP options.
Should you needed to marry a SYN flood with a volumetric assault, you would wish to push a 1:1 ratio of bandwidth out to the sufferer, normally within the type of padded SYN packets. With the arrival of middlebox amplification, this long-held understanding of TCP assaults is not true. Now an attacker wants as little as 1/75th (in some instances) the quantity of bandwidth from a volumetric standpoint, and due to quirks with some middlebox implementations, attackers get a SYN, ACK, or PSH+ACK flood without spending a dime.
Source link


