[ad_1]

Getty Photographs
Malicious hackers have been hammering servers with assaults that exploit the just lately found SpringShell vulnerability in an try to put in cryptomining malware, researchers mentioned.
SpringShell got here to mild late final month when a researcher demonstrated the way it could possibly be used to remotely execute malicious code on servers that run the Spring model-view-controller or WebFlux functions on prime of Java Improvement Equipment variations 9 or increased. Spring is the most widely used Java framework for creating enterprise-level functions in Java. The framework is a part of a sprawling ecosystem that gives instruments for issues like cloud, information, and safety apps.
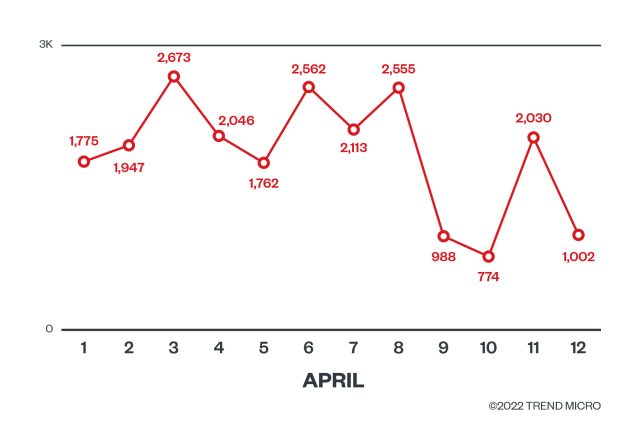
Earlier this month, safety agency Pattern Micro mentioned it started detecting makes an attempt. From April 1 to April 12, firm researchers detected a median of roughly 700 makes an attempt per day to use the vulnerability to put in cryptomining software program. By working the malware on highly effective enterprise servers, criminals can mine Bitcoin or different kinds of digital money utilizing the sources and electrical energy of an unwitting sufferer.
The variety of exploit makes an attempt peaked on April Three at nearly 3,000.
Pattern Micro
The hackers first despatched instructions that had been designed to discern if the weak servers had been working Home windows or Linux. Then they ran exploit code that attempted to put in a kind of interface referred to as an internet shell, which permits a distant consumer to run instructions utilizing a Net-based window.
The URI comparable to the encoded exploit seemed like this, with the online shell being “zbc0fb.jsp” and parameters w and l standing for the Home windows and Linux payloads, that are Base64-encoded.
/zbc0fb.jsp?w=powershell.exe+-NonI+-W+Hidden+-NoP+-Exec+Bypass+-Enc+ &l=echo+
A powershell script then tried to obtain the cryptocurrency miner and execute it. Pattern redacted the script within the following snippet:
$cc="http://"
$sys=-join ([char[]](48..57+97..122) | Get-Random -Depend (Get-Random (6..12)))
$dst="$env:AppData$sys.exe"
The execution stream seemed like this:
1. The firewall is turned off utilizing the netsh utility.
2. Different recognized cryptocurrency miners reminiscent of kthreaddi, sysrv, and sysrv012 are stopped or killed.
3. Different working processes listening on ports 3333, 4444, 5555, 7777, and 9000 are stopped.
4. If the method kthreaddk doesn’t exist, the cryptocurrency miner downloads a binary, sys.exe, from 194[.]145[.]227[.]21 to C:CustomersAppDataRoaming.exe.
5. The cryptocurrency miner then begins the method with a hidden window to keep away from having the consumer observe visible hints of the method being executed.
6. A scheduled job with the title “BrowserUpdate” is created later, working each minute. As well as, the Home windows run key’s modified to run the binary sys.exe.
Pattern Micro researchers don’t know what number of, if any, of the exploit makes an attempt had been profitable. Earlier this month, firm researchers mentioned that they had additionally uncovered makes an attempt to use SpringShell to install the Mirai botnet. Anybody working the Spring model-view-controller or WebFlux functions on the JDK model 9 or increased ought to patch the flaw as quickly as sensible.
Source link


