[ad_1]

Getty Photographs
For greater than a decade, we’ve been promised {that a} world with out passwords is simply across the nook, and but 12 months after 12 months, this safety nirvana proves out of attain. Now, for the primary time, a workable type of passwordless authentication is about to turn out to be out there to the lots within the type of a regular adopted by Apple, Google, and Microsoft that enables for cross-platform and cross-service passkeys.
Password-killing schemes pushed previously suffered from a bunch of issues. A key shortcoming was the shortage of a viable restoration mechanism when somebody misplaced management of telephone numbers or bodily tokens and telephones tied to an account. One other limitation was that almost all options in the end did not be, actually, actually passwordless. As an alternative, they gave customers choices to log in with a face scan or fingerprint, however these programs in the end fell again on a password, and that meant that phishing, password reuse, and forgotten passcodes—all the explanations we hated passwords to start with—didn’t go away.
A brand new method
What’s completely different this time is that Apple, Google, and Microsoft all appear to be on board with the identical well-defined answer. Not solely that, however the answer is simpler than ever for customers, and it is more cost effective for large companies like Github and Fb to roll out. It has additionally been painstakingly devised and peer-reviewed by specialists in authentication and safety.
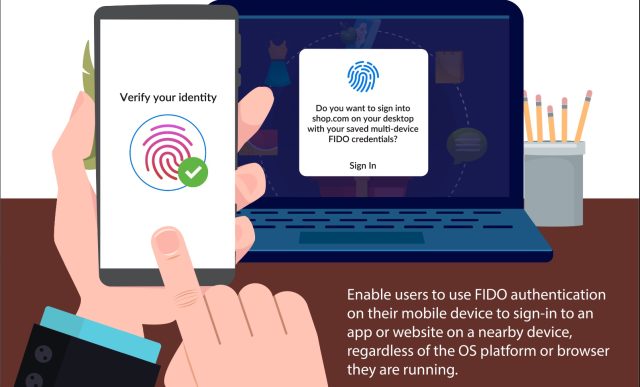
FIDO Alliance
The present multifactor authentication (MFA) strategies have made essential strides over the previous 5 years. Google, for example, permits me to obtain an iOS or Android app that I exploit as a second issue when logging in to my Google account from a brand new system. Based mostly on CTAP—brief for client to authenticator protocol—this technique makes use of Bluetooth to make sure that the telephone is in proximity to the brand new system and that the brand new system is, actually, related to Google and never a web site masquerading as Google. Which means it’s unphishable. The usual ensures that the cryptographic secret saved on the telephone can’t be extracted.
Google additionally supplies an Advanced Protection Program that requires bodily keys within the type of standalone dongles or end-user telephones to authenticate logins from new gadgets.
The massive limitation proper now could be that MFA and passwordless authentication get rolled out otherwise—if in any respect—by every service supplier. Some suppliers, like most banks and monetary companies, nonetheless ship one-time passwords by way of SMS or e-mail. Recognizing that these aren’t safe means for transporting security-sensitive secrets and techniques, many companies have moved on to a way generally known as TOTP—brief for time-based one-time password—to permit the addition of a second issue, which successfully augments the password with the “one thing I’ve” issue.
Bodily safety keys, TOTPs, and to a lesser extent two-factor authentication by way of SMS and e-mail characterize an essential step ahead, however there stay three key limitations. First, TOTPs generated by way of authenticator apps and despatched by textual content or e-mail are phishable, the identical approach common passwords are. Second, every service has its personal closed MFA platform. That signifies that even when utilizing unphishable types of MFA—resembling standalone bodily keys or phone-based keys—a consumer wants a separate key for Google, Microsoft, and each different Web property. To make issues worse, every OS platform has differing mechanisms for implementing MFA.
These issues give technique to a 3rd one: the sheer unusability for many finish customers and the nontrivial price and complexity every service faces when attempting to supply MFA.
Source link


